Below you will find the key ideas from Chapter 10 of CWISA-102
Importance of Security Solutions
- Protection of Data.
- Protection of Users.
- Protection of Machinery.
Security is a crucial component in wireless solutions, especially in user-based networks where mobile devices access network resources. Ensuring the protection of both data and users is a primary concern, and safeguarding their devices is equally important. Regardless of the wireless solution at hand, security should be a top priority throughout the entire lifecycle of the wireless system, from selection and planning to implementation, maintenance, and decommissioning.
ISO/IEC 27033-6: 2016
ISO/IEC 27033-6:2016 outlines common security threats to wireless devices with the aim of defining specific risks, design techniques, and control measures for securing IP wireless networks. Some of the common threats include:
- Unauthorized Access.
- Packets Sniffing.
- Rogue Wireless Access Point.
- Denial of Services Attack.
- Device Tracking.
OWASP IoT Security Threats
- Weak, Guessable or Hardcoded Password.
- Insecure Network Services.
- Insecure Ecosystems Interfaces.
- Lack of Secure Update Mechanism
- Use a insecure outdated components.
- Insufficient Privacy.
- Insecure Data Transfer and Storage.
- Lack of Device Management.
- Insecure Default Settings.
- Lack of Physical Hardening.
CIA
- Confidentiality: This ensures that only authorized individuals or systems should have access to information, and this information should not be shared with third parties without your consent.
- Integrity: Integrity ensures the non-alteration of data. Both data and systems should be protected from intentional, unauthorized, or accidental changes. If any alterations occur, the intended recipient should be able to identify that the data has been altered.
- Availability: Availability ensures that data and systems are operational and accessible when required in a timely manner.
There are several technologies anda practices than can be used to implement CIA in order to secure information systems.
- Encryption: Encrypting data ensure that it is kept confidential, as it can only be accessed by someone who has the correct description key.
- Access Control:Access control can be used to ensure the integrity of data by limiting who can access it and what they can do.
– Backup & Disaster Recovery: Ensuring the availability of data is important for maintaining the operation of an information system. - Firewalls: Firewall are key technology used to secure networks buy blocking unauthorized access and limiting the flow of traffic between different networks.
- Intrusion Detection and Prevention Systems:These system monitor network traffic and all administrator to any suspicious activity or potential security threats.
- Security Information and Event Manager (SIEM): SIEM system collect and analyze security-related data from various sources to identify potential security threats and alert administrator.
Privacy, Non-Repudiation, Authenticity
– Privacy: The terms privacy and confidentiality are often used interchangeably as they share commonalities. However, privacy is more concerned with the individual’s right to keep their personal information to themselves, the right not to be recorded. Conversely, confidentiality is the assurance of data privacy, limiting access to information to authorized entities.
- Non-Repudiation: Non-repudiation prevents a person or entity from denying that they performed a specific action.
- Authenticity: The authenticity principle aims to confirm the identity of the parties involved in a transaction, ensuring that each entity is indeed who it claims to be.
Authentication
With authentication, we can ensure: Confidentiality, Integrity and Non-Reputation. Authentication can happen in different methods base on:
- Something you know.
- Something you are.
- Something you have.
A combination of the above aka multi factor authentication.
Encryption
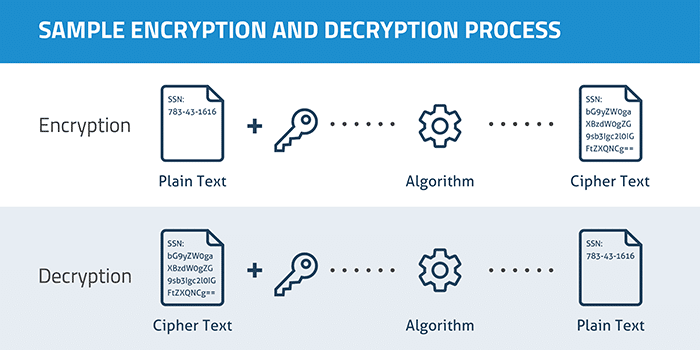
Due to the nature of wireless communications, where signals are transmitted over the air, it is critical to protect these communications from potential eavesdropping attempts where someone might try to listen or spy on the channel. The most effective tool to safeguard against malicious eavesdropping is the use of encryption.
Encryption is the process of converting plaintext or any other form of data into another encoded format that can only be deciphered by another party possessing the decryption key. The primary objective of encryption is to ensure confidentiality. Any third-party entity will only observe the encrypted text or data and will be unable to comprehend the content of the message, even if it is aware of the encryption algorithm.

It’s important to highlight that applying conventional cryptographic encryption algorithms discussed earlier can be challenging for small IoT devices like RFID tags, sensors, smart cards, etc. Therefore, lightweight cryptographic techniques are proposed for these types of systems.
Some examples are:
- Tiny Encryption Algorithm (TEA)
- Extended TEA (XTEA)
- PRESENT
- SIMON
- Scalable Encryption Algorithm (SEA)
Secure Boot
Secure boot is a security feature designed to ensure that a device’s firmware, operating system, and other critical software have not been tampered with or compromised. It protects against threats like bootkits and malware that can infect a device’s firmware and operating system. Secure boot verifies the integrity of the firmware and operating system by checking cryptographic signatures against a trusted database of known good signatures before allowing them to load. This process enhances the overall security of the device.
Implementing secure boot on an IoT device requires the use of a trusted platform module (TPM) or a similar hardware security module. When utilizing TPM hardware, it is used to store the cryptographic keys necessary for verifying the signatures of the device’s firmware and operating system. This ensures the integrity and security of the boot process.
Trusted Software / Signed Software
Trusted software refers to software that is recognized as reliable and secure. It is commonly employed in applications where the software manages sensitive data or performs critical functions. Trusted software is typically developed and maintained by reputable organizations, undergoing extensive testing and validation processes to ensure its security and reliability..
Signed software is software that has undergone digital signing by the developer or publisher. This process is employed to verify the authenticity and integrity of the software. Digital signatures provide a secure way to confirm that the software has not been tampered with and originates from a trusted source.
Segmentation: Traditional (North / South)
Network segmentation is a design approach in networking architecture that involves dividing a network into multiple segments or subnets, each operating as an independent, smaller network. This segmentation is achieved by managing the flow of traffic within the network. The control of traffic within segments can be based on various factors, including location, defining where traffic is allowed or restricted. Additionally, traffic flow can be regulated based on criteria such as traffic type, source, and destination.
Network segmentation should not be mistaken for microsegmentation, a strategy that diminishes an organization’s network attack surface by implementing targeted security controls to restrict east-west communication at the workload level. Although microsegmentation serves specific purposes, it is distinct from standard network segmentation, with several differences between the two, including the following:
- Traditional network segmentation covers a larger segment of the network. Microsegmentation can be used at the device level, which makes it great for internet of things (IoT) and edge devices.
- Network segmentation works with the physical network. Microsegmentation is for virtual networks.
- Network segmentation policies are broad. Microsegmentation policies are much more granular.
- Network segmentation is hardware-based. Microsegmentation is typically software-based.
- Network segmentation limits north-south traffic at the network level. Microsegmentation limits east-west traffic at the workload level.

Zigbee Scurity
Zigbee employs link keys and network keys. Link keys are shared between two communicating devices, primarily utilized for unicast encryption. Network keys, on the other hand, are employed by all devices within the network and are designed for broadcast encryption. In a centralized architecture, a single trust center oversees the entire network, and Zigbee coordinators/routers rely on this trust center to furnish keys and facilitate the provisioning and joining of the network. In a distributed architecture, Zigbee coordinators/routers may function as the trust center for the managed network.

An installation code can be employed for network joining, requiring a match with a code previously registered with the trust center/Zigbee coordinator. This code may be represented as a numerical value or a QR code, serving as a pre-shared key established out-of-band. The install code is eventually a 128-bit number with a 16-bit CRC. The link key is derived from the install code using the Matyas-Meyer-Oseas (MMO) hash function.
Z-Wave Security
All modern Z-Wave devices fall into one of the three security classes.
- S2 Access Control: Highest security (out of band key exchange, encryption of all command transmission)
- S2 Authenticated: Medium security (out of band key exchange, encryption of all command transmission)
- S2 UnAuthenticated: Lowest security (Unencrypted commands transmissions)
Z-Wave comes in two primary security versions: S0 and S2. S2 is required of device certified by the Z-Wave Alliance after April 2017. All Z-Wave devices are Z-Wave 500 and Z-wave 700, both types uses Smart Start specifications for access to the Z-wave network. S2 devices are joined to the network using PIN, Device Specification Key (DSK), or QR code.
LoRa/LoRaWan Security
The LoRa side of the network uses the NwkSKey to secure the integrity of MAC frames. The LoRaWAN uses the AppKey to encrypt payloads all the way to the destination. All encryption is implementing using AS-128-bit.
Devices may join to thee LoRaWAN network using Over the Air Activation (OTAA) or Activation By Personalization (ABP).
With Over-the-Air Activation (OTAA), session keys are negotiated during activation, making it a more secure approach. On the other hand, with Activation by Personalization (ABP), the session keys are hardcoded into the device, requiring the device to be pre-registered on the LoRaWAN network


Deja un comentario