The topic I enjoyed in my process of studying for the CWSP was understanding the hierarchy of keys and how they are derived in the process called the 4-Way Handshake. I think it was one of the most confusing topics since, as mentioned in the book, a single key is not used for encrypting the information.
One of the first points to understand in this process is precisely the hierarchy of keys used in the authentication process.
This process is explained in the CWSP Study and Reference Guide on page 204. The process works from top to bottom, starting with a Master Session Key (MSK). It’s important to view this «Master Session Key» as our seed from which the rest of the keys will be generated. The MSK is created by the 802.1x/EAP process. When implementing a 802.1X/EAP infrastructure, both the authentication server and the supplicant will have information about each other after the mutual exchange of authentication credentials. The MSK is the material of keys/claves derived from the EAP process.
Now, what happens if the network uses a personal authentication method, i.e., PSK? In that case, the passphrase (the Wireless network password) is used to create a Preshared Key (PSK). This PSK would be equivalent to the 802.1x/EAP process that creates the MSK. In other words, our PSK would be our MSK.
It’s important to mention how the PSK is calculated, as the passphrase is just one element in this formula:
PMK=PRF(passphrase, SSID, ssid_length_4096, 256)PMK=PRF(passphrase, SSID, ssid_length_4096, 256)
After the creation of the MSK as a result of the 802.1X/EAP or PSK process, two «master keys» are created.
The «Pairwise Master Key» (PMK) is generated from the MSK; to calculate it, the first 256 bits (0-255) of the MSK are used. In the case of WPA & WPA2 Personal, the PMK must be the same on both ends, i.e., both the AP and the supplicant must have the same key to generate the subsequent keys in this process. The next key generated from the PMK will be the «Pairwise Transient Key» (PTK). The PTK is used to encrypt unicast communications.
The other master key is the «Group Master Key» (GMK); this key is only created with interaction from the authenticator (AP or controller) using a completely private generation process. The key generated by GMK is known as the «Group Transient Key» (GTK). The GTK is used to encrypt multicast and broadcast communications. It’s important to mention that master keys are not used to encrypt data. The master keys are now the seed material for the generation of temporary keys during the 4-Way Handshake process.
Now, once we have clarity on the function of each key and where they come from, let’s move on to the 4-Way Handshake process.
The 4-Way Handshake process, along with the master keys, is responsible for generating the temporary keys PTK and GTK. The process begins right after the authentication and association process of the Open System 802.11.

In the green-colored image, you can observe the packets flowing in the Open System Authentication; that is:
- Probe Request.
- Probe Response.
- Authentication Request.
- Authentication Response.
- Association Request.
- Association Response.
And in red color, you can see the EAPOL packets corresponding to the 4-Way Handshake process. As its name suggests, this process consists of 4 packets, and now we will go through each of them.
As mentioned above, the GMK key and its derivation GTK is a process where only the authenticator acts. To generate or derive the PTK key, the following formula is followed: PTK= PRF (PMK + ANonce + Snonce + AA + SPA)
As we know, PRF is a pseudo-random function, PMK is our Pairwise Master Key, ANonce is a random number belonging to the authenticator, SNonce is a random number belonging to the supplicant, AA is the MAC address of the authenticator, and SPA is the MAC address of the supplicant.
Now, if we analyze the formula, much of the information is already known. For example, the PMK is already known, and the MAC addresses are also known because, as we saw, they were exchanged during the Open System Authentication process. So, the first packet sent in the 4-Way Handshake process (M1) is a frame sent by the authenticator to the supplicant.
ChatGPT
Message 1: The authenticator initiates the 4-Way Handshake process by sending the first EAPOL frame, which contains the ANonce. With this information, the supplicant will have all the necessary inputs to derive the PTK.
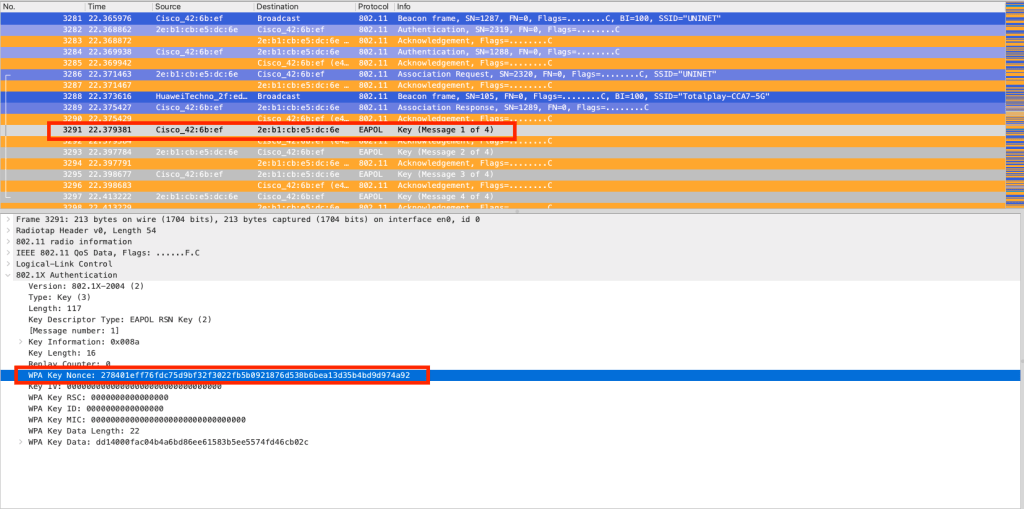
Message 2: Once the device has created its PTK, it sends the SNonce, which is necessary for the AP to generate its own PTK. Message 2 contains a Message Integrity Code (MIC) to ensure that the access point can verify if this message has been tampered with or modified. Once the AP receives the SNonce, it can also generate the PTK for encrypting unicast traffic.

Message 3: EAPOL Message 3 is sent from the AP to the supplicant. The AP creates the GTK without the involvement of the client

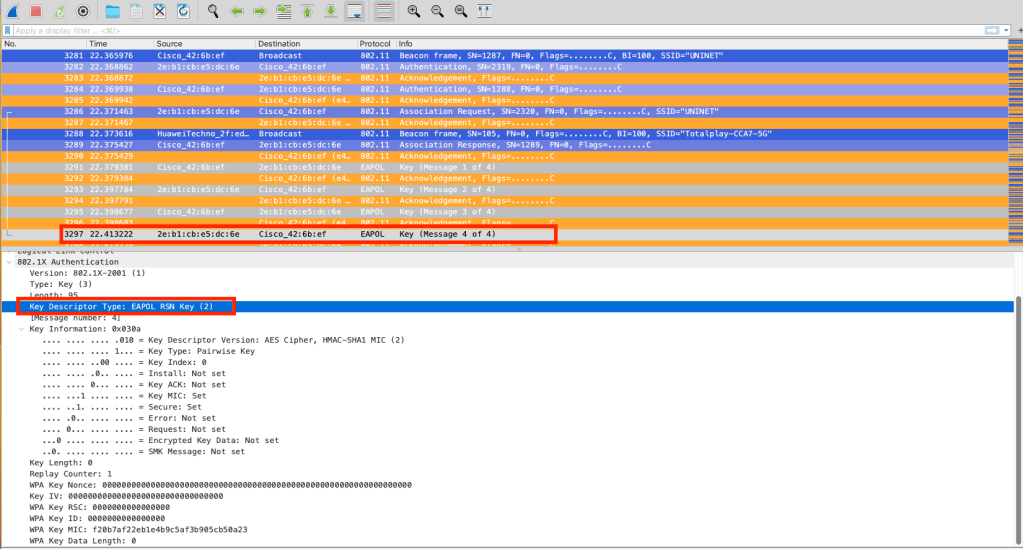
Message 4: The supplicant sends the frame to the authenticator to confirm that the temporary keys have been installed.


Deja un comentario